How do I get valid CompTIA CS0-001 certification dumps? Dumpscertification shares the latest and effective CompTIA CySA+ CS0-001 exam questions and answers, online practice tests, and the most authoritative CompTIA exam experts update CS0-001 exam questions throughout the year. Get the full CS0-001 exam dumps selection: https://www.leads4pass.com/cs0-001.html (414 Q&As). Pass the exam with ease!
CompTIA CySA+ CS0-001 Exam Video
Table of Contents:
- Latest CompTIA CySA+ CS0-001 google drive
- Effective CompTIA CS0-001 exam practice questions
- Related CS0-001 Popular Exam resources
- leads4pass Year-round Discount Code
- What are the advantages of leads4pass?
Latest CompTIA CS0-001 google drive
[PDF] Free CompTIA CS0-001 pdf dumps download from Google Drive: https://drive.google.com/open?id=1SWIrLCSj4qgOfB86uKdQYM0Tdc3XrRlK
CompTIA CSA+ Certification Exam:https://www.comptia.org/certifications/cybersecurity-analyst
About the exam
New CompTIA CySA+ (CS0-002) exam coming in Q2 2020!
CompTIA CySA+ is for IT professionals looking to gain the following security analyst skills:
- Perform data analysis and interpret the results to identify vulnerabilities, threats, and risks to an organization.
- Configure and use threat-detection tools.
- Secure and protect applications and systems within an organization.
Latest updates CompTIA CS0-001 exam practice questions
QUESTION 1
An investigation showed a worm was introduced from an engineer\\’s laptop. It was determined the company does not
provide engineers with company-owned laptops, which would be subject to company policy and technical controls.
Which of the following would be the MOST secure control implement?
A. Deploy HIDS on all engineer-provided laptops, and put a new router in the management network.
B. Implement role-based group policies on the management network for client access.
C. Utilize a jump box that is only allowed to connect to clients from the management network.
D. Deploy a company-wide approved engineering workstation for management access.
Correct Answer: D
QUESTION 2
A security analyst has performed various scans and found vulnerabilities in several applications that affect production
data. Remediation of all exploits may cause certain applications to no longer work. Which of the following activities
would need to be conducted BEFORE remediation?
A. Fuzzing
B. Input validation
C. Change control
D. Sandboxing
Correct Answer: C
QUESTION 3
An organization recently had its strategy posted to a social media website. The document posted to the website is an
exact copy of a document stored on only one server in the organization. A security analyst sees the following output
from a command-line entry on the server suspected of the problem:
Which of the following would be the BEST course of action?
A. Remove the malware associated with PID 773
B. Monitor all the established TCP connections for data exfiltration
C. Investigate the malware associated with PID 123
D. Block all TCP connections at the firewall
E. Figure out which of the Firefox processes is the malware
Correct Answer: A
QUESTION 4
An application development company released a new version of its software to the public. A few days after the release,
the company is notified by end users that the application is notably slower, and older security bugs have reappeared in
the new release. The development team has decided to include the security analyst during their next development cycle
to help address the reported issues. Which of the following should the security analyst focus on to remedy the existing
reported problems?
A. The security analyst should perform security regression testing during each application development cycle.
B. The security analyst should perform end user acceptance security testing during each application development
cycle.
C. The security analyst should perform secure coding practices during each application development cycle.
D. The security analyst should perform application fuzzing to locate application vulnerabilities during each application
development cycle.
Correct Answer: A
QUESTION 5
A cybersecurity analyst is hired to review the security posture of a company. The cybersecurity analyst notices a very
high network bandwidth consumption due to SYN floods from a small number of IP addresses.
Which of the following would be the BEST action to take to support incident response?
A. Increase the company\\’s bandwidth.
B. Apply ingress filters at the routers.
C. Install a packet capturing tool.
D. Block all SYN packets.
Correct Answer: B
QUESTION 6
An employee was conducting research on the Internet when a message from cyber criminals appeared on the screen,
stating the hard drive was just encrypted by a ransomware variant. An analyst observes the following: Antivirus
signatures were updated recently The desktop background was changed Web proxy logs show browsing to various
information security sites and ad network traffic There is a high volume of hard disk activity on the file server SMTP
server shown the employee recently received several emails from blocked senders The company recently switched web
hosting providers There are several IPS alerts for external port scans
Which of the following describes how the employee got this type of ransomware?
A. The employee fell victim to a CSRF attack
B. The employee was using another user\\’s credentials
C. The employee opened an email attachment
D. The employee updated antivirus signatures
Correct Answer: A
QUESTION 7
Several users have reported that when attempting to save documents in team folders, the following message is
received:
The File Cannot Be Copied or Moved – Service Unavailable.
Upon further investigation, it is found that the syslog server is not obtaining log events from the file server to which the
users are attempting to copy files. Which of the following is the MOST likely scenario causing these issues?
A. The network is saturated, causing network congestion
B. The file server is experiencing high CPU and memory utilization
C. Malicious processes are running on the file server
D. All the available space on the file server is consumed
Correct Answer: A
QUESTION 8
Which of the following best practices is used to identify areas in the network that may be vulnerable to penetration
testing from known external sources?
A. Blue team training exercises
B. Technical control reviews
C. White team training exercises
D. Operational control reviews
Correct Answer: A
QUESTION 9
A security analyst with an international response team is working to isolate a worldwide distribution of ransomware. The
analyst is working with international governing bodies to distribute advanced intrusion detection routines for this variant
of ransomware. Which of the following is the MOST important step with which the security analyst should comply?
A. Security operations privacy law
B. Export restrictions
C. Non-disclosure agreements
D. Incident response forms
Correct Answer: D
QUESTION 10
A staff member reported that a laptop has degraded performance. The security analyst has investigated the issue and
discovered that CPU utilization, memory utilization, and outbound network traffic are consuming the laptop resources.
Which of the following is the BEST course of actions to resolve the problem?
A. Identify and remove malicious processes.
B. Disable scheduled tasks.
C. Suspend virus scan.
D. Increase laptop memory.
E. Ensure the laptop OS is properly patched.
Correct Answer: A
QUESTION 11
A cyber incident response team finds a vulnerability on a company website that allowed an attacker to inject malicious
code into its web application. There have been numerous unsuspecting users visiting the infected page, and the
malicious code executed on the victim\\’s browser has led to stolen cookies, hijacked sessions, malware execution, and
bypassed access control. Which of the following exploits is the attacker conducting on the company\\’s website?
A. Logic bomb
B. Rootkit
C. Privilege escalation
D. Cross-site scripting
Correct Answer: D
QUESTION 12
A cybersecurity analyst is conducting packet analysis on the following: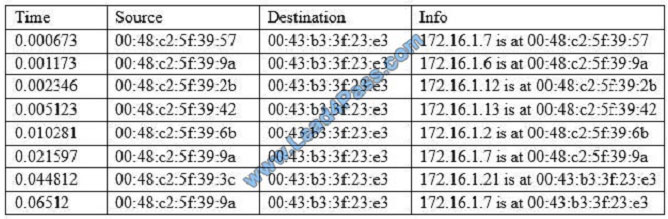
Which of the following is occurring in the given packet capture?
A. ARP spoofing
B. Broadcast storm
C. Smurf attack
D. Network enumeration
E. Zero-day exploit
Correct Answer: A
QUESTION 13
Which of the following is a vulnerability that is specific to hypervisors?
A. DDoS
B. VLAN hopping
C. Weak encryption
D. WMescape
Correct Answer: D
Related CS0-001 Popular Exam resources
| title | youtube | CompTIA | leads4pass | leads4pass Total Questions | related CompTIA blog | |
|---|---|---|---|---|---|---|
| CompTIA CySA+ | leads4pass CS0-001 dumps pdf | leads4pass CS0-001 youtube | CompTIA CSA+ Certification Exam | https://www.leads4pass.com/cs0-001.html | 414 Q&A | Dumpsdemo comptia cs0-001 exam dumps |
leads4pass Year-round Discount Code
What are the advantages of leads4pass?
leads4pass employs the most authoritative exam specialists from CompTIA, Microsoft, Cisco, Oracle, EMC, etc. We update exam data throughout the year. Highest pass rate! We have a large user base. We are an industry leader! Choose leads4pass to pass the exam with ease!
Summarize:
It’s not easy to pass the CompTIA CS0-001 exam, but with accurate learning materials and proper practice, you can crack the exam with excellent results. https://www.leads4pass.com/cs0-001.html provides you with the most relevant learning materials that you can use to help you prepare.