
Lead4Pas provides updated CompTIA CAS-004 dumps for CompTIA CASP+ Exam preparation in VCE learning engine and pdf format. And provide free CAS-004 exam questions.
What is the CompTIA CASP+ certification exam?
Vendor: CompTIA
Exam Code: CAS-004
Exam Name: CompTIA Advanced Security Practitioner (CASP+)
Certification: CompTIA Advanced Security Practitioner
Number of Questions: Maximum of 90 questions
Type of Questions: Multiple choice and performance-based
Length of Test: 165 minutes
Passing score: This test has no scaled score; it’s pass/fail only.
Languages: English and Japanese
Price: $480 USD
CAS-004 dumps: https://www.leads4pass.com/cas-004.html (267 Q&A)
Why use leads4pass CAS-004 dumps?
- Free updates throughout the year, effective immediately (365 days Free Update)
- Covers all CompTIA CASP+ practical exam questions and answers with explanations of difficult problems
- PDF and VCE (most popular learning tools)
- Professional CompTIA certification team, 7 years of exam experience
So why not use the CAS-004 dumps to help you easily and successfully pass the CompTIA CASP+ certification exam? Now, it is highly recommended that you use the CompTIA CASP+ Best Exam Material CAS-004 Dumps https://www.leads4pass.com/cas-004.html, Helping you successfully pass the exam on your first attempt.
Free online practice test for CAS-004 exam questions:
Tips: Verify the answer at the end of the article
Question 1:
An organization is referencing NIST best practices for BCP creation while reviewing current internal organizational processes for mission-essential items. Which of the following phases establishes the identification and prioritization of critical systems and functions?
A. Review a recent gap analysis.
B. Perform a cost-benefit analysis.
C. Conduct a business impact analysis.
D. Develop an exposure factor matrix.
Question 2:
An organization is preparing to migrate its production environment systems from an on-premises environment to a cloud service. The lead security architect is concerned that the organization\’s current methods for addressing risk may not be possible in the cloud environment.
Which of the following BEST describes the reason why traditional methods of addressing risk may not be possible in the cloud?
A. Migrating operations assume the acceptance of all risk.
B. Cloud providers are unable to avoid risk.
C. Specific risks cannot be transferred to the cloud provider.
D. Risks to data in the cloud cannot be mitigated.
Question 3:
A company created an external application for its customers. A security researcher now reports that the application has a serious LDAP injection vulnerability that could be leveraged to bypass authentication and authorization. Which of the following actions would BEST resolve the issue? (Choose two.)
A. Conduct input sanitization.
B. Deploy a SIEM.
C. Use containers.
D. Patch the OS
E. Deploy a WAF.
F. Deploy a reverse proxy
G. Deploy an IDS.
Question 4:
In preparation for the holiday season, a company redesigned the system that manages retail sales and moved it to a cloud service provider. The new infrastructure did not meet the company\’s availability requirements. During a postmortem analysis, the following issues were highlighted:
1.
International users reported latency when images on the web page were initially loading.
2.
During times of report processing, users reported issues with inventory when attempting to place orders.
3.
Despite the fact that ten new API servers were added, the load across servers was heavy at peak times.
Which of the following infrastructure design changes would be BEST for the organization to implement to avoid these issues in the future?
A. Serve static content via distributed CDNs, create a read replica of the central database and pull reports from there, and auto-scale API servers based on performance.
B. Increase the bandwidth for the server that delivers images, use a CDN, change the database to a non-relational database, and split the ten API servers across two load balancers.
C. Serve images from an object storage bucket with infrequent read times, replicate the database across different regions and dynamically create API servers based on load.
D. Serve static-content object storage across different regions, increase the instance size on the managed relational database, and distribute the ten API servers across multiple regions.
Question 5:
During a remodel, a company\’s computer equipment was moved to a secure storage room with cameras positioned on both sides of the door. The door is locked using a card reader issued by the security team, and only the security team and department managers have access to the room. The company wants to be able to identify any unauthorized individuals who enter the storage room by following an authorized employee.
Which of the following processes would BEST satisfy this requirement?
A. Monitor camera footage corresponding to a valid access request.
B. Require both security and management to open the door.
C. Require department managers to review denied-access requests.
D. Issue new entry badges on a weekly basis.
Question 6:
A company is preparing to deploy a global service.
Which of the following must the company do to ensure GDPR compliance? (Choose two.)
A. Inform users regarding what data is stored.
B. Provide opt-in/out for marketing messages.
C. Provide data deletion capabilities.
D. Provide optional data encryption.
E. Grant data access to third parties.
F. Provide alternative authentication techniques.
Question 7:
A SOC analyst is reviewing malicious activity on an external, exposed web server. During the investigation, the analyst determines specific traffic is not being logged, and there is no visibility from the WAF for the web application. Which of the following is the MOST likely cause?
A. The user agent client is not compatible with the WAF.
B. A certificate on the WAF is expired.
C. HTTP traffic is not forwarding to HTTPS to decrypt.
D. Old, vulnerable cipher suites are still being used.
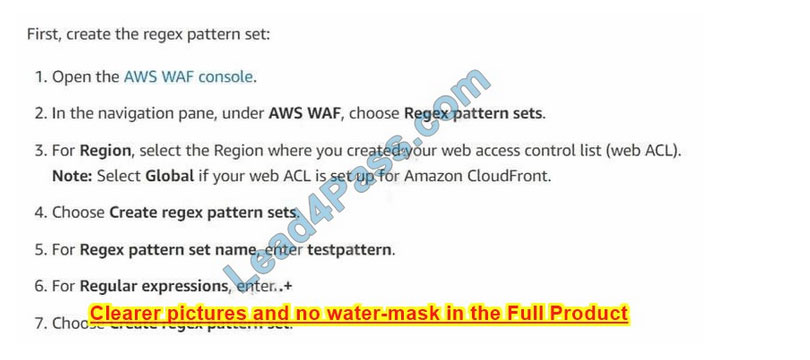
Question 8:
A security analyst is reviewing the following output:

Which of the following would BEST mitigate this type of attack?
A. Installing a network firewall
B. Placing a WAF inline
C. Implementing an IDS
D. Deploying a honeypot
Question 9:
Which of the following terms refers to the delivery of encryption keys to a CASB or a third-party entity?
A. Key sharing
B. Key distribution
C. Key recovery
D. Key escrow
Question 10:
An organization is implementing a new identity and access management architecture with the following objectives:
1.
Supporting MFA against on-premises infrastructure
2.
Improving the user experience by integrating with SaaS applications
3.
Applying risk-based policies based on location
4.
Performing just-in-time provisioning
Which of the following authentication protocols should the organization implement to support these requirements?
A. Kerberos and TACACS
B. SAML and RADIUS
C. OAuth and OpenID
D. OTP and 802.1X
Question 11:
Which of the following allows computation and analysis of data within a ciphertext without knowledge of the plaintext?
A. Lattice-based cryptography
B. Quantum computing
C. Asymmetric cryptography
D. Homomorphic encryption
Question 12:
A company is looking to fortify its cybersecurity defenses and is focusing on its network infrastructure. The solution cannot affect the availability of the company\’s services to ensure false positives do not drop legitimate traffic. Which of the following would satisfy the requirement?
A. NIDS
B. NIPS
C. WAF
D. Reverse proxy
Question 13:
A disaster recovery team learned of several mistakes that were made during the last disaster recovery parallel test. Computational resources ran out at 70% of the restoration of critical services. Which of the following should be modified to prevent the issue from reoccurring?
A. Recovery point objective
B. Recovery time objective
C. Mission-essential functions
D. Recovery service level
Question 14:
A technician is reviewing the logs and notices a large number of files were transferred to remote sites over the course of three months. This activity then stopped. The files were transferred via TLS-protected HTTP sessions from systems that do not send traffic to those sites.
The technician will define this threat as:
A. a decrypting RSA using obsolete and weakened encryption attack.
B. a zero-day attack.
C. an advanced persistent threat.
D. an on-path attack.
Question 15:
A security engineer thinks the development team has been hard-coding sensitive environment variables in its code. Which of the following would BEST secure the company\’s CI/CD pipeline?
A. Utilizing a trusted secrets manager
B. Performing DAST on a weekly basis
C. Introducing the use of container orchestration
D. Deploying instance tagging
……
Verify answer:
| Numbers: | Q1 | Q2 | Q3 | Q4 | Q5 | Q6 | Q7 | Q8 | Q9 | Q10 | Q11 | Q12 | Q13 | Q14 | Q15 |
| Answers: | C | C | BD | A | A | AB | B | A | B | A | C | B | B | A | A |
Successfully pass the CompTIA CASP+ certification exam, become one of them, achieve a career leap, and improve the actual salary, which is the dream of all professionals.
Then, you only need to choose the CAS-004 dumps provided by leads4pass to help you realize your dream, click here to download the latest CAS-004 exam questions and answers and help you pass the CompTIA CASP+ certification exam easily.