With the help of latest and authentic Cisco Network Management 600-199 dumps exam questions, you can find the best 600-199 exam preparation kit here. “Securing Cisco Networks with Threat Detection and Analysis” is the name of Cisco Network Management https://www.leads4pass.com/600-199.html exam dumps which covers all the knowledge points of the real Cisco exam.
Get your Cisco Network Management 600-199 dumps exam preparation questions in form of 600-199 PDF. Lead4pass is the best site for providing online preparation material for 600-199 SCYBER – Cisco exam. You can download Cisco Network Management 600-199 dumps pdf training material from lead4pass and pass the Cisco 600-199 exam in the first attempt.
Cisco 600-199 dumps pdf google drive: https://drive.google.com/open?id=13lt5gENk0I7FGrqHPv5fYEpmk47yW-tg
Cisco 600-512 dumps pdf google drive: https://drive.google.com/open?id=0B_7qiYkH83VRNlNxSEJLNlo0Wmc
Free latest Cisco 200-105 dumps pdf questions and answers, high quality Cisco 200-105 dumps exam practice files and youtube. Download the best useful Cisco Network Management 600-199 dumps vce software online to have a free try.
High Quality Cisco Network Management 600-199 Dumps Exam Questions And Answers (Q1-Q20)
QUESTION 1
Refer to the exhibit.
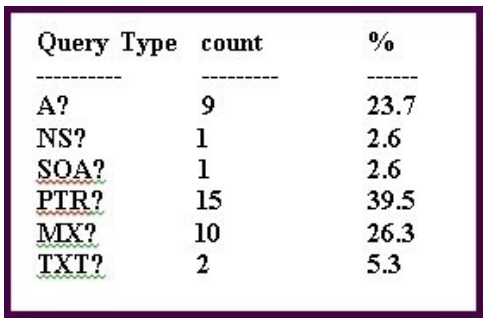
Which DNS Query Types pertains to email?
A. A?
B. NS?
C. SOA?
D. PTR?
E. MX?
F. TXT?
Correct Answer: E
QUESTION 2
A server administrator tells you that the server network is potentially under attack. Which piece of information is critical to begin your network investigation?
A. cabinet location of the servers
B. administrator password for the servers
C. OS that is used on the servers
D. IP addresses/subnets used for the servers
Correct Answer: D
QUESTION 3
Which describes the best method for preserving the chain of evidence?
A. Shut down the machine that is infected, remove the hard drive, and contact the local authorities.
B. Back up the hard drive, use antivirus software to clean the infected machine, and contact the local authorities.
C. Identify the infected machine, disconnect from the network, and contact the local authorities.
D. Allow user(s) to perform any business-critical tasks while waiting for local authorities.
Correct Answer: C
QUESTION 4
Which will be provided as output when issuing the show processes cpu command on a Cisco IOS router?
A. router configuration
B. CPU utilization of device
C. memory used by device processes
D. interface processing statistics
Correct Answer: B
QUESTION 5
Refer to the exhibit.
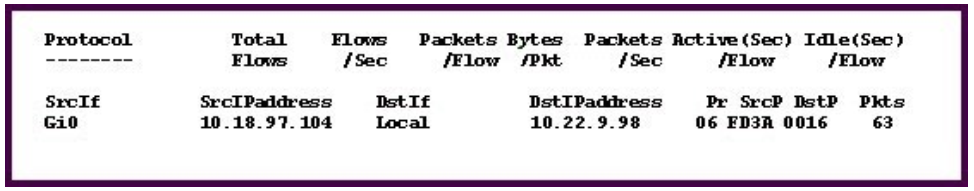
Which protocol is used in this network traffic flow?
A. SNMP
B. SSH
C. DNS
D. Telnet
Correct Answer: B
QUESTION 6
Which two types of data are relevant to investigating network security issues? (Choose two.)
A. NetFlow
B. device model numbers
C. syslog
D. routing tables
E. private IP addresses
Correct Answer: AC
QUESTION 7
In the context of a network security device like an IPS, which event would qualify as having the highest severity?
A. remote code execution attempt
B. brute force login attempt
C. denial of service attack
D. instant messenger activity
Correct Answer: A
QUESTION 8
Which event is likely to be a false positive? 600-199 dumps
A. Internet Relay Chat signature with an alert context buffer containing #IPS_ROCS Yay
B. a signature addressing an ActiveX vulnerability alert on a Microsoft developer network documentation page
C. an alert for a long HTTP request with an alert context buffer containing a large HTTP GET request
D. BitTorrent activity detected on ephemeral ports
Correct Answer: B
QUESTION 9
Given a Linux machine running only an SSH server, which chain of alarms would be most concerning?
A. brute force login attempt from outside of the network, followed by an internal network scan
B. root login attempt followed by brute force login attempt
C. Microsoft RPC attack against the server
D. multiple rapid login attempts
Correct Answer: A
QUESTION 10
If a company has a strict policy to limit potential confidential information leakage, which three alerts would be of concern? (Choose three.)
A. P2P activity detected
B. Skype activity detected
C. YouTube viewing activity detected
D. Pastebin activity detected
E. Hulu activity detected
Correct Answer: ABD
QUESTION 11
Which event is actionable?
A. SSH login failed
B. Telnet login failed
C. traffic flow started
D. reverse shell detected
Correct Answer: D
QUESTION 12
Which would be classified as a remote code execution attempt?
A. OLE stack overflow detected
B. null login attempt
C. BitTorrent activity detected
D. IE ActiveX DoS
Correct Answer: A
QUESTION 13
Given the signature “SQL Table Manipulation Detected”, which site may trigger a false positive?
A. a company selling discount dining-room table inserts
B. a large computer hardware company
C. a small networking company
D. a biotech company
Correct Answer: A
QUESTION 14
Which is considered to be anomalous activity?
A. an alert context buffer containing traffic to amazon.com
B. an alert context buffer containing SSH traffic
C. an alert context buffer containing an FTP server SYN scanning your network
D. an alert describing an anonymous login attempt to an FTP server
Correct Answer: C
QUESTION 15
If an alert that pertains to a remote code execution attempt is seen on your network, which step is unlikely to help?
A. looking for anomalous traffic
B. looking for reconnaissance activity
C. restoring the machine to a known good backup
D. clearing the event store to see if future events indicate malicious activity
Correct Answer: D
QUESTION 16
Refer to the exhibit.
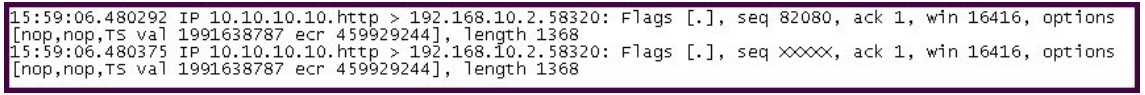
In the tcpdump output, what is the sequence number that is represented by XXXXX?
A. 82080
B. 82081
C. 83448
D. 83449
E. 98496
F. 98497
Correct Answer: C
QUESTION 17
Refer to the exhibit.
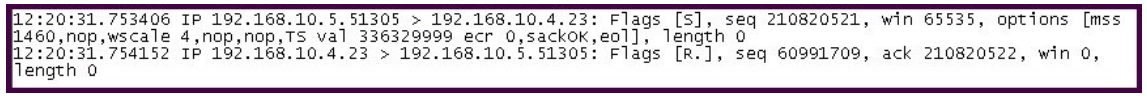
Based on the traffic captured in the tcpdump, what is occurring?
A. The device is powered down and is not on the network.
B. The device is reachable and a TCP connection was established on port 23.
C. The device is up but is not responding on port 23.
D. The device is up but is not responding on port 51305.
E. The resend flag is requesting the connection again.
Correct Answer: C
QUESTION 18
Which three statements are true about the IP fragment offset? 600-199 dumps (Choose three.)
A. A fragment offset of 0 indicates that it is the first in a series of fragments.
B. A fragment offset helps determine the position of the fragment within the reassembled datagram.
C. A fragment offset number refers to the number of fragments.
D. A fragment offset is measured in 8-byte units.
E. A fragment offset is measured in 16-byte units.
Correct Answer: ABD
QUESTION 19
Which two tools are used to help with traffic identification? (Choose two.)
A. network sniffer
B. ping
C. traceroute
D. route table
E. NetFlow
F. DHCP
Correct Answer: AE
QUESTION 20
Which three symptoms are best used to detect a TCP SYN flood attack? (Choose three.)
A. high memory utilization on target server
B. large number of sockets in SYN_RECV state on target server
C. network monitoring devices report large number of unACKed SYNs sent to target server
D. target server crashes repeatedly
E. user experience with target server is slow or unresponsive
Correct Answer: BCE
Cisco 600-199 dumps pdf google drive: https://drive.google.com/open?id=13lt5gENk0I7FGrqHPv5fYEpmk47yW-tg
Cisco 600-512 dumps pdf google drive: https://drive.google.com/open?id=0B_7qiYkH83VRNlNxSEJLNlo0Wmc
The best and most updated latest Cisco Network Management 600-199 dumps pdf training resources which are the best for clearing 600-199 exam test, and to get certified by Cisco Network Management https://www.leads4pass.com/600-199.html, download one of the many PDF readers that are available for free with high pass rate.
Useful Cisco Network Management 600-199 dumps vce youtube: https://youtu.be/35WaC0y8UI8